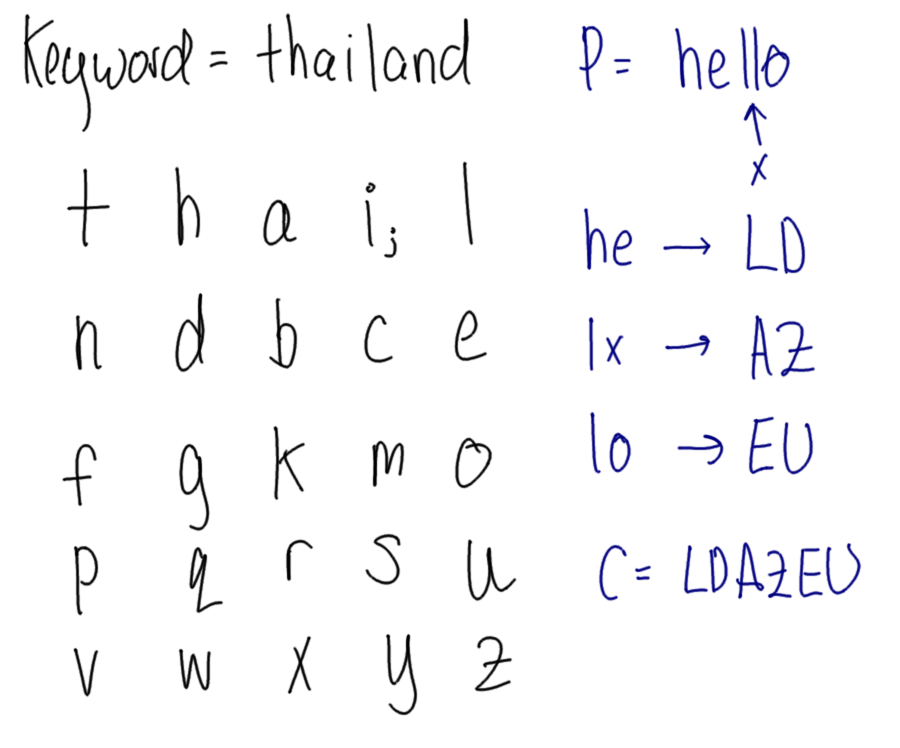
Example Of Network Security. For example, only a telnet proxy can copy, forward, and filter telnet traffic. In the recent times, network security has become the central topic of cyber security with many organisations inviting applications of people who have skills in this area.
Customize which certificate authorities (ca) are trusted for. It includes both software and hardware technologies. The most basic example of network security is password protection where the user of the network oneself chooses.
A Real World Example Of An Unsegmented Network And Resulting Attack Is The Massive Target Data Breach Of 2013.
Access to the network is managed by adequate network security, which targets many threats and then arrests them from spreading or entering the network. Network security is a broad term that covers a multitude of technologies, devices and processes. It may instead be that the operators have different preferences when it comes to how a 3gpp ue should connect to epc via that.
Identified Within Offensive Security’s Network.
For example, only a telnet proxy can copy, forward, and filter telnet traffic. Telecommunication network security is defined by the following layers that determine the network security experience of end users. The most basic example of network security is password protection where the user of the network oneself chooses.
Msiexec /I Kaspersky Network Agent.msi /Qn , Where Stand For The List Of Space Separated Installation Parameters With Their Values (For Example, Prop1=Prop1Val Prop2=Prop2Val).</P>
In this example, you have created a network firewall and a nat gateway, and you have an amazon ec2 instance with traffic routed to the internet through the network firewall and nat gateway. Customize which certificate authorities (ca) are trusted for. The drawing tools of network security diagrams solution are very useful for network security design.
On The Project’s Properties You Will Find The Sdk You Are Compiling.
These settings can be configured for specific domains and for a specific app. Use augmented rules in the source, destination, and port fields of a rule. You can combine multiple ports and multiple explicit ip addresses and ranges into a single, easily understood security rule.
The Malware Lurked In The Hvac Network For Two Months Before.
Firewalls control incoming and outgoing traffic on networks, with predetermined security rules. Types of network security protections firewall. Example test scenarios for security testing:
0 Comments